Cloudridge Consulting
10 Steps to Achieve SOC 2 Compliance for Small and Medium-Sized Businesses
Step 1: Understand the Scope of SOC 2 Compliance
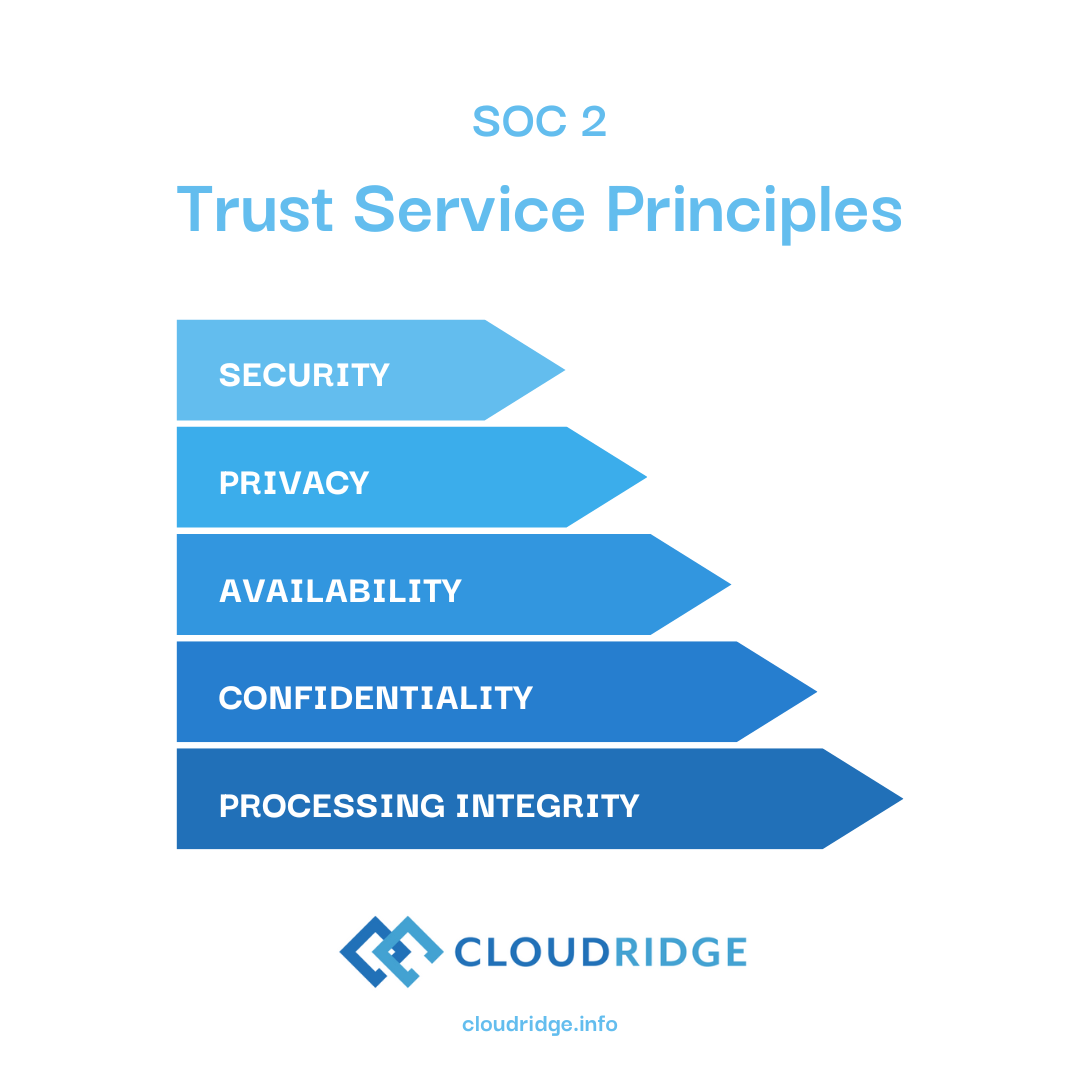
Charting a path forward is always the first step to a successful journey! When pursuing SOC 2 compliance, you’ll want to take some time to understand the scope of the requirements. SOC 2 focuses on five trust principles: security, availability, processing integrity, confidentiality, and privacy. Familiarize yourself with these principles and determine which ones are applicable to your business operations. This will help you identify the specific controls and processes you’ll need to implement along the way.
Step 2: Conduct a Risk Assessment
Every organization will have inherent risks and potential vulnerabilities – the key to mitigating these is understanding what they are. Performing a thorough risk assessment will help to identify these vulnerabilities and risks within your unique organization. This process involves evaluating your current information systems, policies, and procedures to explore which areas may have room for improvement or additional controls. By conducting a comprehensive risk assessment, you can develop a solid understanding of your organization’s security risks – which will help you to focus your efforts accordingly.
Step 3: Develop Your Policies and Procedures
Congratulations! You’ve made it to arguably the most essential and exciting part of the SOC 2 process: creating and implementing your policies and procedures. Whether you prepare these internally, or obtain support from an expert advisor, these documents will perform the essential task of outlining the specific controls and processes that your organization will follow to meet the trust principles. Your policies and procedures will need to cover areas such as access controls, change management, incident response, and data protection. Keep in mind, the work isn’t done when you hit “save”! It is imperative that these documents are communicated effectively to all employees and regularly updated as needed.
Step 4: Implement Security Controls
Now that you understand SOC 2 scope, have insight into your businesses’ potential risks and vulnerabilities, and have clear policies and procedures prepared, it’s time to implement your security controls. These controls should align with security principles and address areas such as network security, system monitoring, data encryption, and physical security. Make sure to select controls that are suitable for your organization’s size and industry, and set a schedule to regularly test and monitor their effectiveness.
Step 5: Monitor and Review
Unfortunately, nothing in security is truly a “set-it-and-forget-it” system. In order to maintain SOC 2 compliance, you’ll need to ensure continuous monitoring and regular review of your controls and processes. This includes conducting internal audits, vulnerability assessments, and penetration testing to identify any gaps or weaknesses. By monitoring and reviewing your systems and controls, you’ll empower your team to promptly address any issues and make necessary improvements.
Step 6: Train Your Team
No matter what systems and processes you may have in place, they will only be effective if every single member of your staff understands their role in protecting the business. Employee awareness and training play a crucial role in SOC 2 compliance. It is essential to educate your employees about the policies, procedures, and security controls in place. Regular training sessions can help reinforce the importance of data protection, privacy, and the role each employee plays in maintaining SOC 2 compliance.
Step 7: Engage an Independent Auditor
On the journey to achieving SOC 2 compliance, you may find that an independent auditor can be a valuable guide and resource. An auditor can assess your organization’s controls and processes, provide guidance on areas for improvement, and ultimately issue a SOC 2 report. Working with an independent auditor demonstrates your commitment to maintaining the highest standards of security and trust.
Step 8: Remediate and Improve
After undergoing an audit, it is common to identify areas that will require remediation or improvement. It is crucial that your team devote the necessary time and attention to address these gaps promptly, and develop an action plan to tackle any necessary corrections or improvements. By continuously bolstering and refining your controls and processes, you can ensure ongoing SOC 2 compliance and strengthen your overall security posture.
Step 9: Obtain a SOC 2 Report
Once your organization has successfully implemented the necessary controls and undergone an audit, you can obtain a SOC 2 report. This report provides valuable assurance to your customers and partners that your organization has met the trust principles outlined in SOC 2. The report can be shared with potential clients during the sales process and can give your business a competitive edge.
Step 10: Ongoing Compliance Upkeep
The three great essentials to achieve anything worth while are, first, hard work; second, stick-to-itiveness; third, common sense.
– Thomas Edison
SOC 2 compliance is not a one-and-done achievement – it requires ongoing commitment and diligence. In order to maintain compliance, you’ll need to continuously monitor and review your controls, conduct regular audits, and stay up-to-date with any changes in the SOC 2 framework. But, by maintaining ongoing compliance, you can demonstrate your dedication to protecting your customers’ data and maintaining a high level of trust.
Navigating the SOC 2 process can be challenging and labor-intensive, but you don’t have to forge a path all alone! By partnering with an expert consultant, you can gain the support and confidence to conquer the challenges of achieving SOC 2 compliance. Ready to charge ahead? Reach out today and take the first step towards your SOC 2 compliance goal.
